Mobile security
threats include both physical and software-based threats that can
compromise the data on smartphones, tablets and similar mobile
devices. Like viruses and spyware that can infect your PC, there are
a variety of security threats that can affect mobile devices.
30 Nov 2018
27 Nov 2018
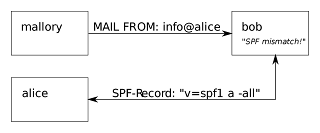
Sender Policy Framework (SPF)
Sender Policy Framework (SPF) is a method of fighting
spam emails. SPF is designed to prevent forged or spoofed emails being sent by
checking and validating that the sender is authorised to send email from the domain
they're claiming to be from.
21 Nov 2018
Firefox Monitor will let you know if your online account was breached
Data breaches are
common for online services. Most people don’t know they have been
affected by a data breach. This makes it difficult for affected
people to secure their online accounts as they don’t know they’re
insecure in the first place. This is why Firefox Monitor
was launched to notify users when they visit a site that has been
breached in the past.
24 May 2018
Telegram messenger security bots, channels and groups
Telegram messenger is a free cloud-based mobile and desktop messaging app with a focus on security and speed. With Telegram, you can send messages, photos, videos and files of any type (doc, zip, mp3, etc.), as well as create Groups for up to 100,000 people or Channels for broadcasting to unlimited audiences. Telegram supports end-to-end encrypted voice calls. you can get more info about Telegram here.
6 May 2018
Twitter advises users to change password now
If you’re using Twitter you should change your password. Twitter has advised that more than 330 million users on its platform should change their passwords due to a bug. Twitter identified a bug that stored passwords unmasked (unscrambled, thus in clear/plain text) in an internal log.
Labels:
bug,
encryption,
password,
twitter,
vulnerability
25 Apr 2018
Microsoft launches Windows Defender Browser Protection extension for Google Chrome
 |
| warning when you visit malicious website |
21 Jan 2018
MasterCard introduces cards with embedded fingerprint sensors
MasterCard has unveiled a payment card with a fingerprint sensor embedded. It's currently being tested in South Africa and hopes to be rolled out to the rest of the world by the end of 2017. This will depend on the results of additional trials in Europe and Asia Pacific, to be effected in the coming months.
9 Jan 2018
Locky ransomware spreading via Facebook Messenger
Ransomware is a sophisticated malware that infects your computer, encrypts files and denies victim access to his/her files until a ransom is paid within a stipulated time. Read information on what Ransomware is, how criminals infect your computer with Ransomware, and what you can do to stay safe. All that information is here.
6 Jan 2018
Microsoft’s Skype Serving malicious ads on windows
Users running Microsoft’s Skype VoIP client on Windows are being served malicious ads trying to push a fake Adobe Flash Player update that eventually leads to a malware infection.
Phishing campaign to steal PayPal users’ identity
There have been countless phishing attacks on PayPal users, but of late the attack has got sophisticated with emails that look real as well as the fake website. Recently phishing attacks were targeting Gmail users and they could fool even the IT pros.
5 Jan 2018
Full List of Cisco Products Vulnerable to CIA Hack found in Wikileaks ‘Vault 7’ Docs
Below is a full list of Cisco products Vulnerable to CIA Hack found in Wikileaks ‘Vault 7’ Docs of secret C.I.A. hacking tools.
Labels:
cisco,
switch,
vault7,
vulnerability
Hundreds of Cisco Switch Models Vulnerable to CIA Hack found in Wikileaks ‘Vault 7’ Docs
Cisco Systems said it has found a critical vulnerability affecting the IOS and IOS XE software inside hundreds of models of its switches. The vulnerability can allow an attacker to remotely gain full control or cause a reload of an affected device.
Subscribe to:
Posts (Atom)